- Home
- Technologies
- Self-Recognition Agents
Self-Recognition Agents (SRAs)
AVIRTEK researchers have developed an Anomaly Behavior Analysis (ABA) methodology to recognize any non-self behavior in computers, protocols, users, or applications. The ABA methodology has been successfully applied to analyze the behavior of different network protocols (IP, TCP, UDP), wireless networks, HTTP, DNS, and email protocols. In this technology, we use the ABA methodology to analyze the operations of the cyber footprint data structures. To explain our ABA-based Self-Recognition methodology, we will describe two examples: Anomaly detection in the Domain Name System (DNS) protocol (application layer protocol) and detection of malicious components embedded in data objects (e.g., files, HTML, XML, Image, etc.).
AVIRTEK’s ABA approach for the DNS protocol is based on continuously monitoring and analyzing the temporal behavior of the DNS protocol to detect any anomalous behavior that might be triggered by DNS attacks. The DNS protocol according to RFC1034 [9] and RFC 1035 [10] is a Query-Response protocol. It means that a DNS server will listen to its dedicated port (standard UDP port 53) and for each Query it receives, it sends back an appropriate Response.
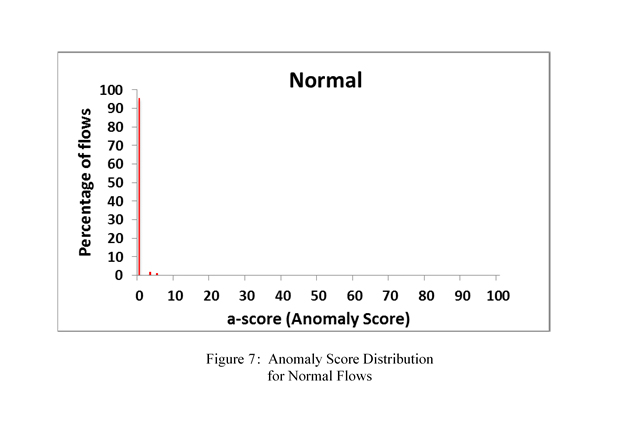
In anomaly behavior analysis, it is necessary to characterize the normal DNS traffic in order to detect abnormal behaviors that exploit the existing vulnerabilities in the DNS protocol. We use machine learning techniques to learn the normal transitions when the DNS protocol is operating normally. In the training mode, we generate normal DNS traffic as well as abnormal traffic. During this phase, the n-grams of the DNS traffic are generated and the statistical properties of each pattern are stored in the database. If during the testing mode, the statistical properties of the observed n-gram (anomaly score) are significantly different from those stored for normal n-gram DNS traffic, it will be considered abnormal.
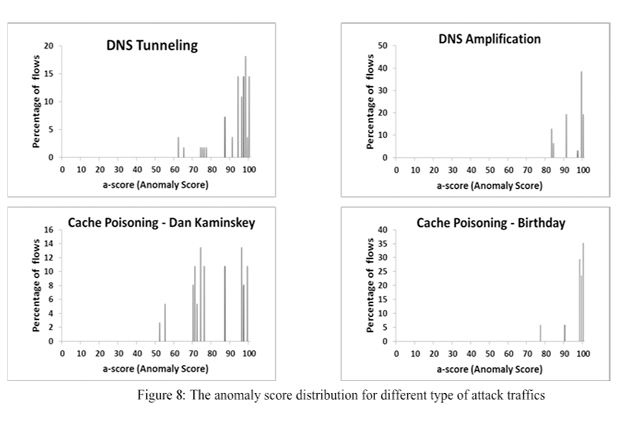
We evaluated the ABA for the DNS protocol with different types of DNS attacks (e.g., birthday attack and Dan Kaminsky cache poisoning, DNS Amplification, and DNS Tunneling) that were detected accurately with no false alarms. Figures 7 and 8 indicate the distribution of the anomaly score (a-score) for normal and DNS attack flows. The X axis shows the anomaly score and the Y axis represents the percentage of flows which match that score.
It is clear from these diagrams that the normal and abnormal traffic are properly separated and consequently can detect DNS attacks with almost no false alarms
With an award from the US Air Force, AVIRTEK applied ACS methodology to detect the existence of malicious components embedded within any data objects or files.