


Autonomic Cyber Security (ACS)
ACS is for:
• Individuals, Small/Medium size organizations that do not have fortune 500-level cyber budget
• Enterprise data centers
• Government, specially DoD networks, datacenters, and tactical networks and services
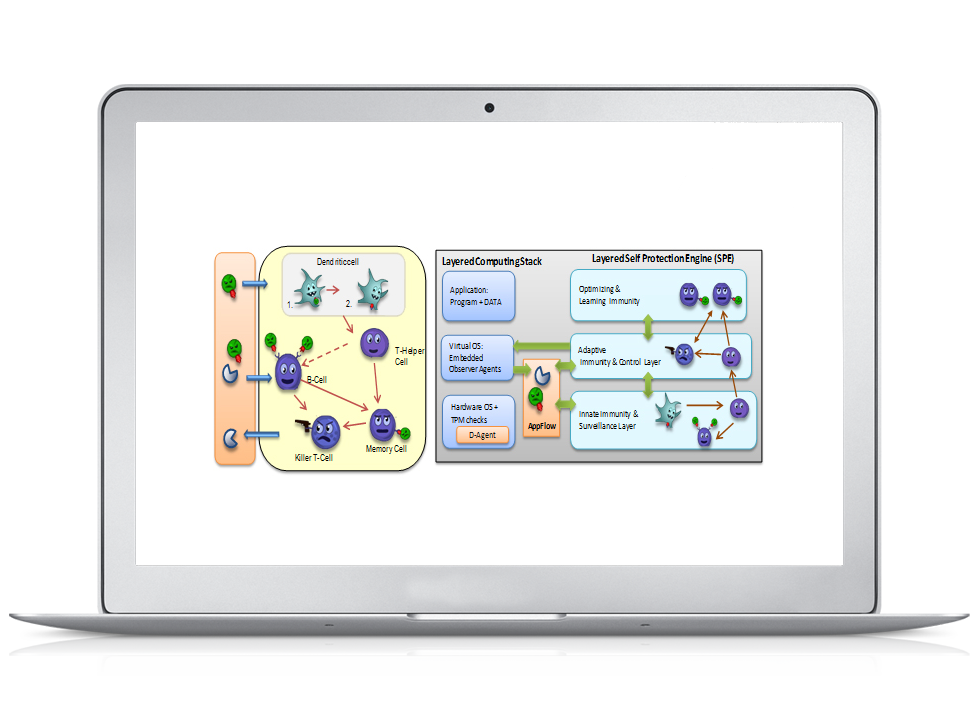

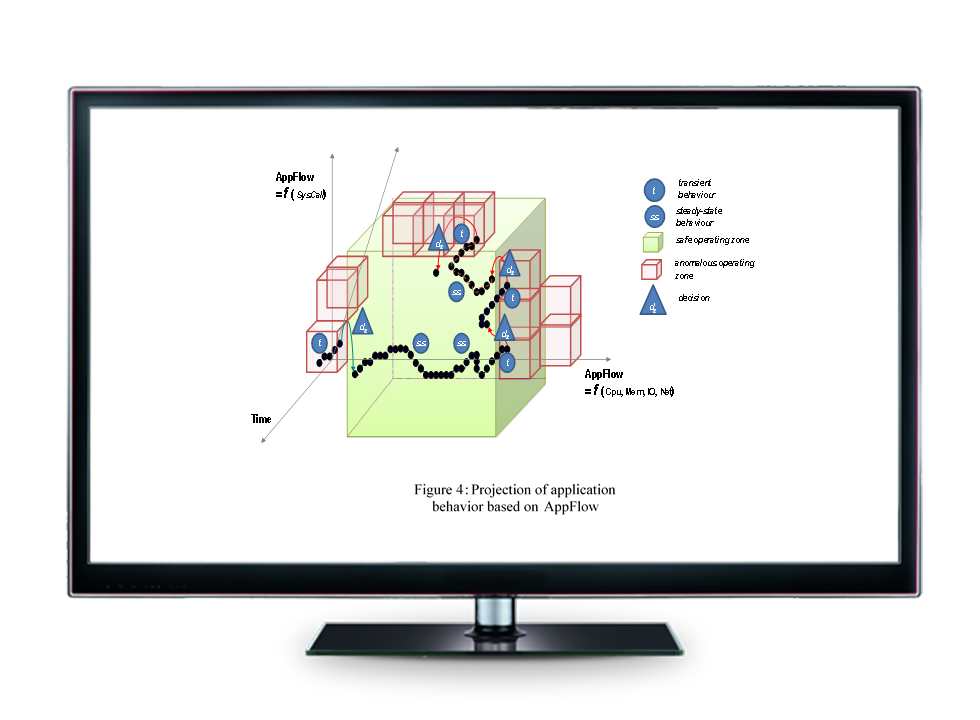
Anomaly Behavior Analysis (ABA)
Detect accurately with low false alarms threats that might be triggered by insiders or externals, known or unknown cyberattacks

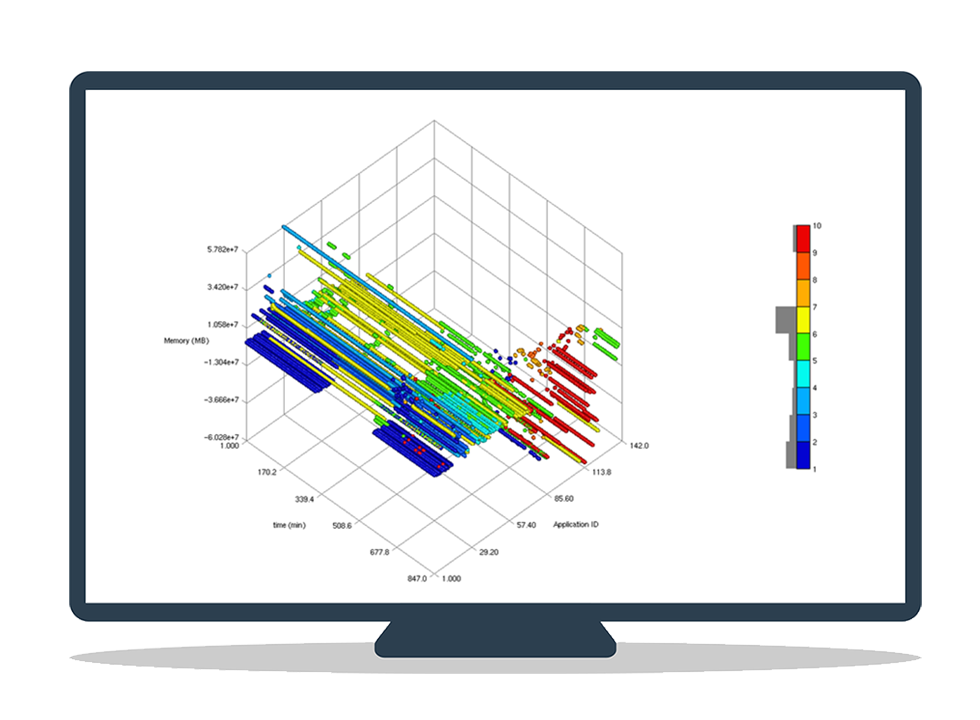
User Cyber Footprint (UCF)
Integrate Biometrics (keyboard and mouse usage patterns) with system, network, and software metrics to uniquely identify how each user interact with its computer environment and how he/she types and mouses to detect insider threats and malicious activities


Autonomic Cyber Security (ACS)
The exponential increase of network connections, bandwidth, users, processing and global dependence on the Internet has greatly increased vulnerabilities of Information Technology (IT) infrastructure to more and more sophisticated and motivated attacks. In spite of drastically increased funding for R&D and deployment of information assurance defenses, reports of attacks on, and damage to the IT Infrastructure are growing at an accelerated rate.




